 |
 |
| Satisfied with your back up solution? |
| Here are 3 Questions to Consider! |
 |
When it comes to back up options, users
are spoiled for choice! Indeed, deciding
whether to upgrade or strengthen backup
software can be difficult and requires |
|
|
 |
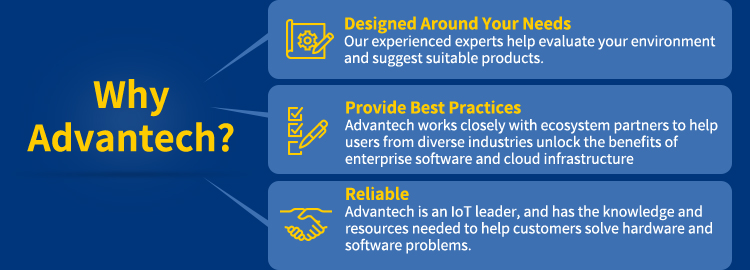
| assessing which aspects are most important to the user. Advantech recommends taking the following three questions into consideration before making a decision. |
|
|
 |
 |
Is your backup reliable enough to
"set it and forget it?" |
|
| Reliability is a primary concern in IT. Why are scheduled backups ineffective? Backup typically occupies most of a hard drive’s available space. In such cases, is data duplication workable? Failover switching sometimes fails during internal testing. In such cases, how do we manage disaster recovery? Most users expect backup solutions to provide peace of mind and “set it and forget it” functionality. |
|
|
 |
Does your backup solution defend against cyberattacks? |
|
| Situations arise in which systems encounter reinfection despite users recovering them quickly during cyberattacks. These situations occur when users don’t have functions that block hacker or ransomware attacks from outside. Email phishing scams are the most prevalent and successful attack methods in use today (representing around 90% of attacks). This makes finding backup solutions that include security functions an important task. |
|
 |
|
 |
 |
Does your back up solution work
efficiently? |
|
| Efficiency is an important IT division KPI. This makes easy and efficient recovery processes a key product consideration. Most backup products require a certain number of clicks to accomplish recovery or failover. Likewise, many solutions either lack the granularity for specific recoveries or the scalability for bulk restores. These considerations make switching to practical user-friendly backup solutions a top priority. |
|
|
 |
Security and
Management
Comprehensive yet simple
endpoint management
toolkit conserves IT
resources |
Upgrade Workload
Protection
Antivirus scans in backups,
decreases load on
protected devices |
Instant Data
Recovery
Prevent downtime with
near-zero RPOs and RTOs for
all users and applications |
|
|
 |










